#
INTRODUCTION
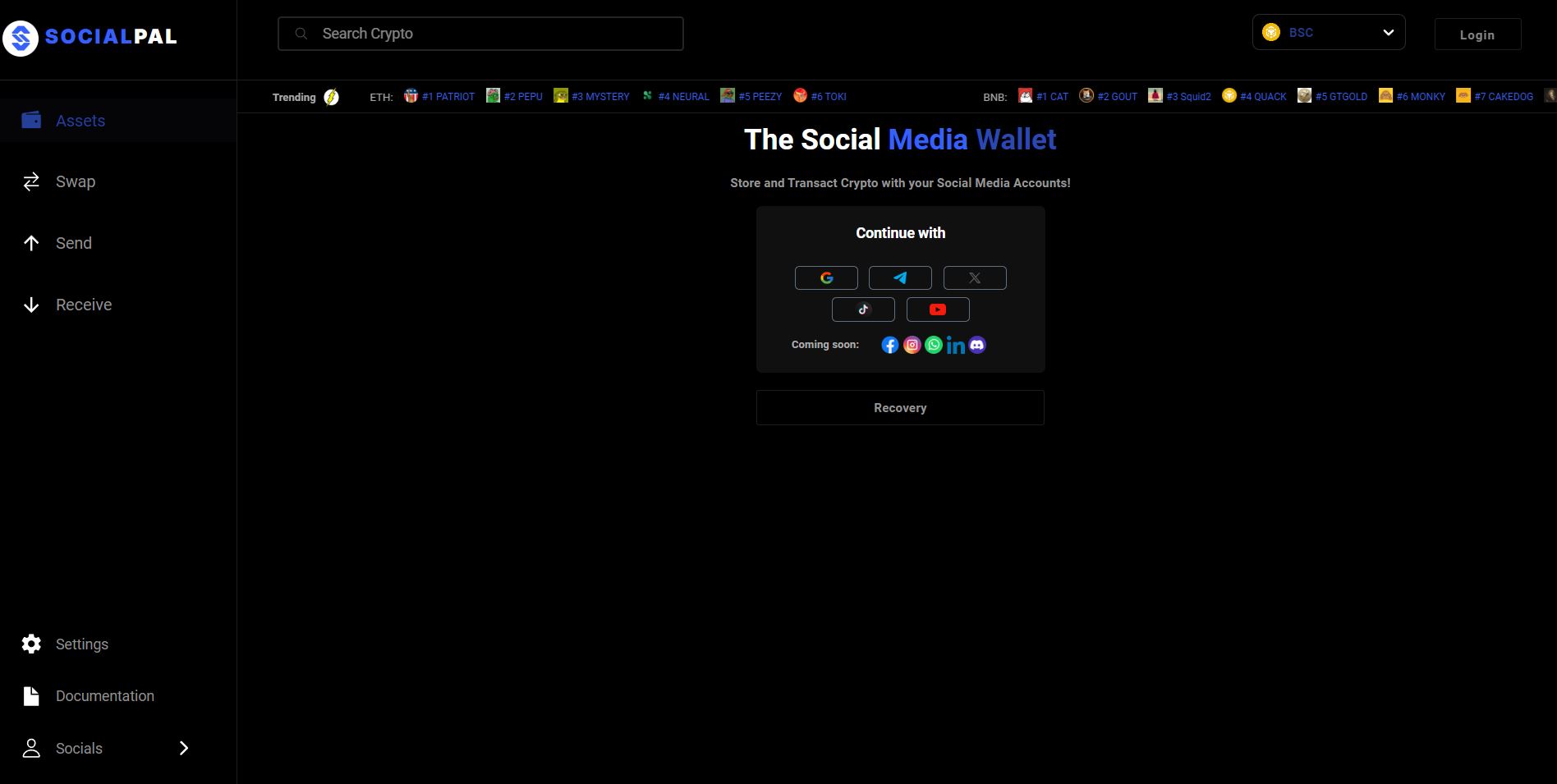
SocialPal is a next-generation blockchain wallet poised to transform digital asset management. Our web application enables users to transact effortlessly using their favourite social media usernames. By combining the versatility and security of blockchain technology, SocialPal provides a unique and enhanced user experience. Our innovative web app allows for seamless transactions directly through the browser. Users can easily create a wallet by connecting their Google, Telegram, or Twitter (X) accounts, enabling them to send, receive, and swap tokens with ease. What distinguishes SocialPal is its ability to facilitate transactions using social media handles, making it simple for users to connect with friends and family on familiar platforms. This approach streamlines the process, offering a user-friendly web-based solution for everyday crypto transactions.
We understand the significance of social media platforms in people’s lives as essential hubs for communication, information sharing, and community engagement. Leveraging this widespread adoption, SocialPal enables payments to users across multiple platforms, including Telegram, Gmail, Twitter (X), and soon Facebook, WhatsApp, and more. Our web application allows users to effortlessly set up their wallets using existing social media accounts, eliminating the need for additional registrations or complex verification processes. By leveraging users’ familiarity with their favourite social media platforms, SocialPal ushers in a new era of usability and accessibility for blockchain wallets. This overview aims to highlight SocialPal's key features, benefits, and solutions to address the limitations of existing wallets.
Safety and security are paramount for blockchain wallets, and SocialPal places them as our top priorities. SocialPal recognizes the importance of safeguarding users' funds from internal and external threats, so we are taking extraordinary measures to ensure the highest level of protection. SocialPal uses an encrypted wallet with an AES password generated from two different hashes on different objects stored via state of the art identity-based encryption management system with restricted localized access and automatic credential removal. It’s a zero-knowledge application level process, and to guarantee long-term security, we plan to engage a top-tier audit company for a complete system audit and release a bug bounty program to the community.